Vulnerability Assessment Platform
Vulnerability Assessment platform allows for the detection of vulnerabilities in your organisation assets using many ways. Code analysis vulnerability tools analyze coding bugs. Audit vulnerability tools can find well-known rootkits, backdoor, and trojans.
Our Vulnerability Assessment platform helps secure your network:
If an attack starts by modifying device networking configuration, the tools will be able to identify and put a stop to it. They assist you with regulatory compliance with their ability to detect out-of-process changes, audit configurations, and even correct violations.
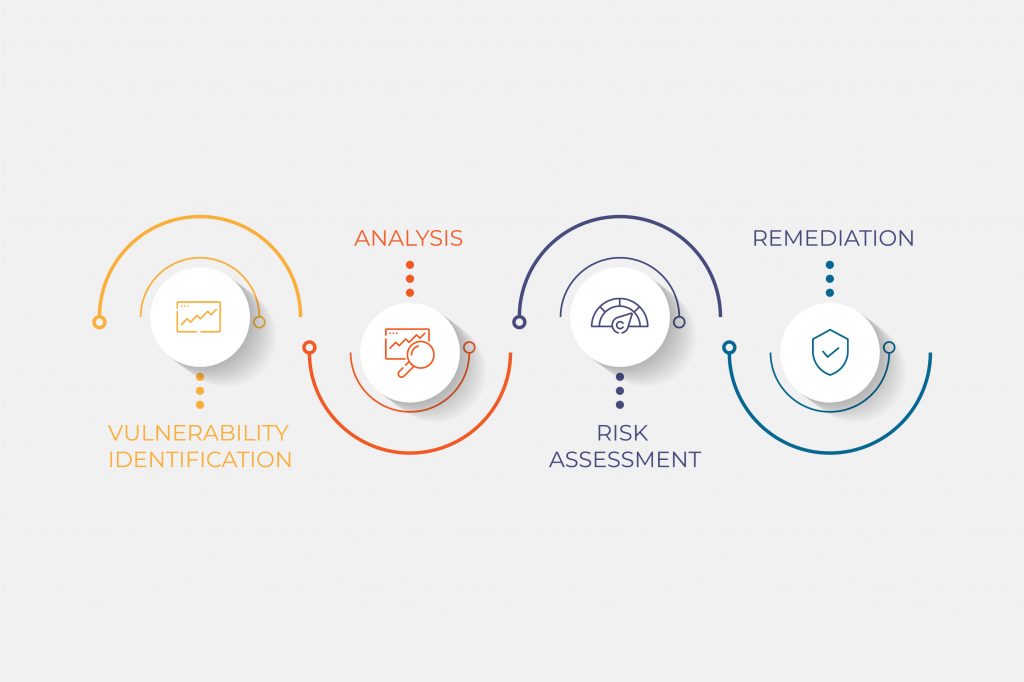
We follow a systematic process as outlined below:
Step 1 – Begin the process by obtaining the necessary permission from stakeholders.
Step 2 – Perform vulnerability scanning using our tool. Make sure to save all the outputs from those vulnerability tools.
Step 3 – Analyse the output and decide which vulnerabilities identified could be a possible threat. You can also prioritize the threats and find a strategy to mitigate them.
Step 4 – Make sure you document all the outcomes and prepare reports for stakeholders.
Step 5 – Fix the vulnerabilities identified.
Advantages of our tool:
Our tool keeps systems secure from external threats. Other benefits include:
- Affordable – Many vulnerability scanners are available free of charge.
- Quick – Assessment takes a few hours to complete.
- Automate – can use automated functions available in the vulnerability tools to perform scans regularly without manual involvement.
- Performance – vulnerability scanners perform almost all the well-known vulnerability scan.
- Cost/Benefit – reduce cost and increase benefits by optimizing security threats.
Vulnerability Testing Decreases Risk:
Our Vulnerability Assessment tool identify and deal with security vulnerabilities before it’s too late and help manages your security requirements.