WHAT WE PROVIDE
Our Services
All Services

Network Architecture Review
Every business or company has its set of intra as well as inter-network communication established to enable the transfer of data and information. We, at Inventonus, identify this conjuncture in bringing to you our Network Architecture Review efficacies designed to judge the scalability of your company’s communication standards.

Penetration Testing
Penetration testing refers to a simulated instance of a cyber-attack against a website or web application to check for its vulnerabilities and loopholes. Inventonus, your trusted information system security analyser and provider ponders on providing quality penetration testing services to your venture transpiring..

SOC 1
SSAE 18 issued by AICPA contains the rules for conducting an attestation of a service organization’s internal controls and issuing report on System and Organization Controls (SOC) report. Service auditors are required to follow these rules when conducting SSAE 18 with trust service criteria.

SOC 2
We help organizations in implementation and attestation of SOC 2.
Report on trust service criteria for controls over the security, availability, confidentiality, processing integrity, and/or privacy
Type 1 report under SOC 1 refers to design of controls
Type 2 report under SOC 1 refers to Auditor opinion on the controls

SOC as a Service
Monitoring security in an inter connected world can be challenging task. Tracking consistent threats and attacks from external and internal sources need to be monitored. This job is made easy with implementation of SIEM which in tracking attacks and threats. Security operations Center (SOC) ease out not only implementation of SIEM and but also help in monitoring of such events.

Security Awareness Training
Security Awareness Training refers to making your employees educated on computer and software security. Today, SAT has become an integral part of any organisation for ensuring the privacy of its information system.
We at Inventonus understand this conjuncture and thereby bring forth our state of the experts who strive to provide top-notch awareness training to your working personnel.

Vulnerability Assessment
Organizational loopholes, be minor or major, are common to all major insignias and you are no exception. So, opting for vulnerability analysis services takes centre stage which aids your company in identifying the weak spots and take necessary action. Inventonus brings to you our vulnerability assessment services which will help you in the following two ways:
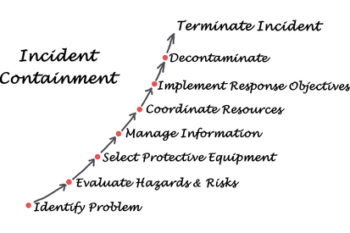
Incident Management
Unprecedented incidents can often lead to hefty losses for an organisation. Thus, incident management on broader level becomes imperative, and this is where we, at Inventonus, come to the scene. With our able team of incident management experts at disposal, we analyse your organisation’s past incidents and records and then take steps accordingly.

Information Security Audit
Every company, belonging to small-scale, medium scale or large-scale category, performs a periodic security audit of the organisation. This is especially true when companies are looking to assess the reliability of their information system standards and therefore delve in search of security audit services. We at Inventonus emerge to be the silver lining in this respect..

ISO 27001 Consultation & Implementation
Securing the information standards of your organisation deems to be your primary aim as a business owner. In this respect, the ISO 27001 implementation appears to be highly profitable. This is where we at Inventonus come to the scene in providing our customers with proficient consultation on the understanding and implementation of ISO 27001 standards.

IOT Security
IOT or Internet of Things brings forth the privilege of connecting multiple devices under a single controller network. While this enhances clientele satisfaction and works efficiency manifold, it also opens up opportunities for third-party intrusion as well. So, we at Inventonus have come with our IOT security services that aim to safeguard your network from unprecedented breaches.

Governance, Risk Management & Compliance
Irrespective of an organisation, GRC forms the three pillars of organisational management. Broadly categorised as Governance, Risk management and Compliance, precise implementation of all three standards ensure a seamless implementation of all operations within an organisation.Cyber Security deals significantly with data

Secure Code Review
Secure code review is the ultimate and finest way of filtering code based faults in any company’s information security system. We at Inventonus offer impeccable security code review services which aim at delivering state of the art services to our clients.Our experts sit for an in detail scrutinisation of your company’s security-based code and analyse the same for any flaws or faults.

Web Application Security Testing
With the advent of fast and high-speed internet, web applications are deeming to be the future of this World Wide Web Consortium. While every website is striving towards presenting their services through a web application, risks and vulnerabilities are also increasing every day. So, Inventonus has brought forth its web application security testing techniques

Data & Lifecycle Management
DLM or Data & Life Cycle Management Processes deals with the flow of data from the initial stages of an information system, until the time when the system becomes obsolete. Our in-house experts of DLM services at Inventonus delve into the credible storage and retrieval of data during times of requirement.At Inventonus, we follow a hierarchical storage management approach which allows us to organise and store data

Mobile Application Security
Mobile applications are the need of the hour considering the advent of fast and affordable internet connection. This is why, most businesses are looking to render their businesses into a mobile format considering Google’s preferences for the same as well.We, at Inventonus, identify this conjuncture and bring forth our mobile application security services.